NetFlow
What is NetFlow?
NetFlow is a proprietary network protocol originally developed for Cisco routers by Cisco Systems. It is widely used to collect metadata about the IP traffic flowing across network devices such as routers, switches and hosts. By monitoring and analyzing NetFlow data, administrators can gain insights into network traffic flow and volume.
The NetFlow protocol’s datagram carries information such as the source and destination ports, source IP addresses, destination IP addresses, IP protocol, and the IP service type. If administrators collect flow records from all flow-enabled network devices — routers, switches, etc. — they gain visibility and an understanding of where network traffic data is coming from and going to, how much traffic is being generated, who is consuming most bandwidth, and more. These data points can be used for anomaly detection, monitoring bandwidth usage, capacity planning, and to validate the effectiveness of QoS (Quality of Service) policy.
How can NetFlow data be collected and analyzed?
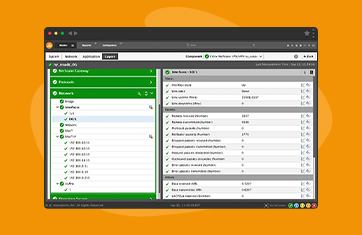
Typically network administration teams employ NetFlow monitoring tools for flow data collection and analysis. A NetFlow monitoring tool uses a flow collector to gather network packets and export the flow data from flow-enabled devices. A NetFlow analyzer is then used to process the raw flow data into meaningful insights through visualizations, real-time alerts, and historical reports.
Monitoring NetFlow requires three components:
What monitoring tools are popular to collect and analyze NetFlow data?
Popular monitoring tools supporting NetFlow analysis include: SolarWinds NetFlow Traffic Analyzer (NTA), eG Enterprise NetFlow Analyzer, PRTG Network Monitor, ManageEngine NetFlow Analyzer, Scrutinizer by Plixer, Cisco Stealthwatch, Dynatrace and others.
Features and use cases vary greatly, particularly in the amount of human operator interaction and manual configuration needed. The more sophisticated AIOps based platforms such as eG Enterprise can provide automated deployment, metric thresholds and alerts out-of-the-box, so issues and anomalous behaviors are proactively and continuously monitored.
What are the differences between NetFlow versions (e.g., NetFlow v5, v9, IPFIX)?
The first NetFlow version 1 was supported in all the initial flow monitoring releases. Versions 2, 3, and 4 were only usable as internal releases. NetFlow V5 became widely used with its fixed packet format and is still supported by various routers. Versions 7 and 8 had a few improvements and they are no longer used in practice.
NetFlow v9 offers significant improvements over v5 and introduced template-based flow exporting, offering greater flexibility and extensibility. V9 allows export of customizable flow records using templates, which reduces the data export overhead and supports additional fields beyond the fixed ones in v5. NetFlow v9 also supports IPv6 flow records, MPLS (Multi-Protocol Label Switching) information, and additional Layer 2 information like VLAN ID. The template-based structure enables the inclusion of vendor-specific or custom fields, making it more adaptable to different network environments.
IPFIX (IP Flow Information Export) is an IETF standard (RFC 7011) that is based on the concepts of NetFlow v9. It is essentially NetFlow v9 with standardization. IPFIX is designed to be vendor-neutral, making it compatible with a wide range of network devices and flow analysis tools from different vendors. It supports various encodings for the flow data export, including binary and IPFIX Message Format (IPFIX over TCP and UDP). IPFIX is commonly used in environments where standardization and interoperability are important.
IPFIX is sometimes colloquially referred to as NetFlow v10 although Cisco do not release a “NetFlow v10”.
What insights can be gained from NetFlow data?
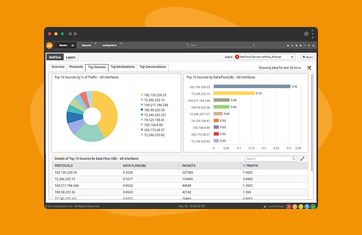
A NetFlow analyzer obtains different compositions of data from the incoming flow data. You can gain insights such as:
This flow data can help you find out
Key use cases and benefits of NetFlow
There are many good applications for which NetFlow is leveraged, key use cases and benefits include:
Can NetFlow be used in cloud environments or with virtualized networks?
Often in cloud environments or virtualized environments provided by a third-party the network behavior and component metrics are deliberately obfuscated or abstracted from the IT administrator, usually for security reasons and because networking is assumed to be the responsibility of the platform (Cloud or virtualized infrastructure) provider. In these cases, administrators should take care to ensure their monitoring and observability tools have a solid and comprehensive integration with the platform vendors APIs and interfaces to ensure access to networking insights.
On-premises virtualized environments can usually retain full access to the raw NetFlow data and components and moreover correlate such data with monitoring data from the virtualization layers, applications and hardware too.